Easy to set up
Saving you time is what ESET Special is all about. Our software offers straightforward deployment, simplified navigation and effortless updates.
Set-and-forget protection keeps users, systems and data safe so you can devote time to other business priorities.

Multi-platform protection
Protects endpoints, mobiles, remote workforce, file servers and virtual machines. Combines powerful security with minimal system demands to keep your business running smoothly.
Designed with SMBs in mind, ESET endpoint special protection provides seamless protection across multiple platforms and processes.

Cloud-based convenience
Get a single-point overview of your network security. Receive notifications as incidents occur and react immediately, with secure access via web browser wherever you are.
Manage the security of your endpoints*, while reducing costs and simplifying your network protection, either from the cloud or via on-premise console.
*ESET Cloud Administrator does not currently support mobile and virtualization security management, although these products may still be installed and activated with your license.
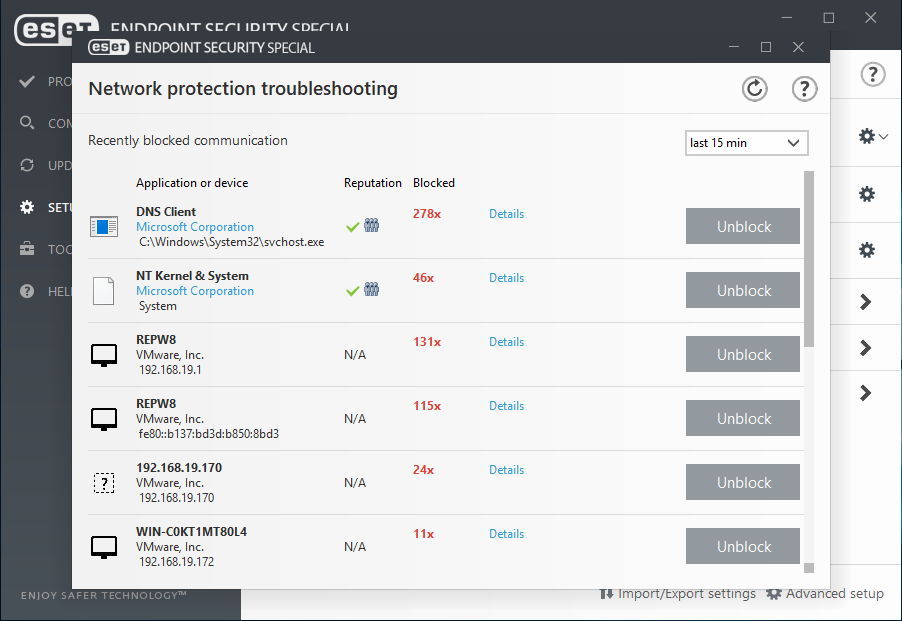
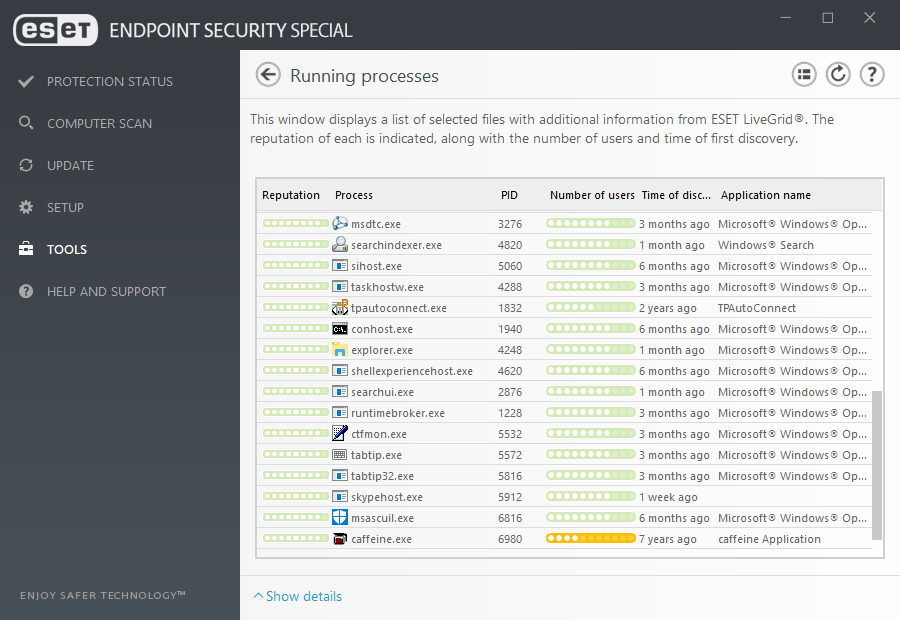
Easy-to-use product interface
Endpoint Special protection features
Explore our multilayered approach to balancing performance, detection and false positives.

Ransomware shield
Monitors and evaluates all executed applications based on their behavior and reputation. Designed to detect and block processes that resemble the behavior of ransomware.

Advanced memory scanner
A unique ESET Special technology which effectively addresses an important issue of modern malware—heavy use of obfuscation and/or encryption. Advanced Memory Scanner monitors the behavior of a malicious process and scans it once it decloaks in memory.

Behavioral detection
ESET's Host-based Intrusion Prevention System (HIPS) monitors system activity and uses a pre-defined set of rules to recognize and stop suspicious system behavior.

Two-way firewall
Prevents unauthorized access to the company network. Provides anti-hacker protection, data exposure prevention, and enables defining trusted networks—making all other connections, such as to public Wi-Fi, restricted by default.

Botnet protection
Detects malicious communication used by botnets, and at the same time identifies the offending processes. Any detected malicious communication is blocked and reported to the user.

Exploit blocker
Monitors typically exploitable applications (browsers, document readers, email clients, Flash, Java, and more). Rather than just aiming at particular CVE identifiers, it focuses on exploitation techniques. When triggered, the threat is blocked immediately on the machine.

Network attack protection
Improves detection of known vulnerabilities on the network level. It constitutes another important layer of protection against spreading malware, network-conducted attacks, and exploitation of vulnerabilities for which a patch has not yet been released or deployed.

In-product sandbox
ESET's in-product sandbox assists in identifying the real behavior hidden underneath the surface of obfuscated malware. Utilizing this technology, ESET Special solutions emulate different components of computer hardware and software to execute a suspicious sample in an isolated virtualized environment.

Light footprint
Optimized for high performance, ESET maintains superior protection while keeping system resource demands and false positives at an industry low.
Award-winning record of endpoint special protection excellence
ESET has been winning industry awards for complete endpoint special protection for more than 20 years. Our multi-platform security solutions include web control, firewall and antispam, providing advanced layers of protection for endpoints and networks.

Awarded top marks, named lightest endpoint security special solution.

Endpoint Security Special 5/5 Stars in all categories in SC Magazine’s review.

AAA award in Enterprise Endpoint Special Protection test.
Common security concerns
System requirements and license information
Supported operating systems
For computers
For file servers
For mail servers
For virtual environments
Flexible license
Mix and match your licenses as needed
ESET Special Unilicense covers all the bases, allowing you to mix and match endpoint special protection without wasting a single license.
Add additional devices at any time
You can purchases licenses for additional computers, laptops, mobile devices and servers any time.
Transfer a license to another computer
You can transfer a valid ESET Special license to a completely new computer from the original one. In addition, you can switch from one OS to another.
Switch to a different platform at any time
It's easy to switch your protection from one platform to another any time during the license term, without having to purchase additional licenses.
Products included with your license
ESET Endpoint Security Special
ESET Endpoint Antivirus Special
ESET File Security Special
ESET Mail Security Special
ESET Virtual Security Special
Benefits of central management
Cloud-based Runs in an ESET-maintained cloud environment
Manage the security of your endpoints, while reducing costs and simplifying your network protection, all from the cloud.
- Setup and deployment within minutes
- No need for additional hardware or software
- Single point of network security management
- Secure access via web browser from anywhere
- Recommended for small businesses up to 250 devices
On-premise Runs on your physical or virtualized environment
Real-time visibility for on-premise and off-premise endpoints as well as full reporting for ESET enterprise-grade solutions.
What IT pros are saying

"Runs better than ANY other AV I have EVER used, blocks the issues before the user can attempt to use the questionable files."

"I enjoy the continuous protection, automatic updates, and comparably small size of this program in comparison to other options."

"The things I enjoy most about their products is how light they run on my clients systems and how easily they are to manage and configure."